Android Devices Now Being Targeted By LodaRAT Windows

A former Windows RAT (Remote Access Trojan) that had the abilities of credential-stealing has now been upgraded and its scope has been widened to cover and target Android device users to increase the attacker’s espionage motives.
Researchers from Cisco Talos, in a blog post, said that “The developers of LodaRAT have added Android as a targeted platform. A new iteration of LodaRAT for Windows has been identified with improved sound recording capabilities.”
The researchers further explained that the group of attackers/hackers behind the malware, known as the Kasablanca, is believed to be responsible for deploying the new RAT during an ongoing campaign aimed at targeting users from Bangladesh.
The identity of the threat actor hasn’t been clear and so is the reason why users and organizations of Bangladesh are specifically targeted for this campaign.
Loda was first reported in May 2017 by Proofpoint and is an AutoIt malware normally conveyed by means of phishing baits which is prepared to execute a wide scope of commands intended to record sound, video, and gather other confidential and sensitive data, with various variations intended towards password theft and stealing browser cookies.
The most recent variants named Loda4Android and Loda4Windows are quite similar as they come with a full arrangement of information gathering features that involves a stalker application. Notwithstanding, the Android malware is likewise extraordinary, as it especially ignores methods frequently utilized by banking Trojans, such as manhandling Accessibility APIs to record on-screen tasks and activities.
Other than having a similar command-and-control (C2) framework for both Android and Windows, the assaults, which initiated in October 2020, have focused on banks and carrier-grade voice-over-IP software merchants, with pieces of information highlighting the malware developer being situated in Morocco.
The attackers/hackers likewise made a heap number of tricks of social engineering, varying from typo squatted domains to noxious RTF (Rich Text Format) reports attached in emails, which when opened, initiates a contamination chain that uses a memory corruption flaw in Microsoft Office, that has been registered as CVE-2017-11882, to download the last payload.
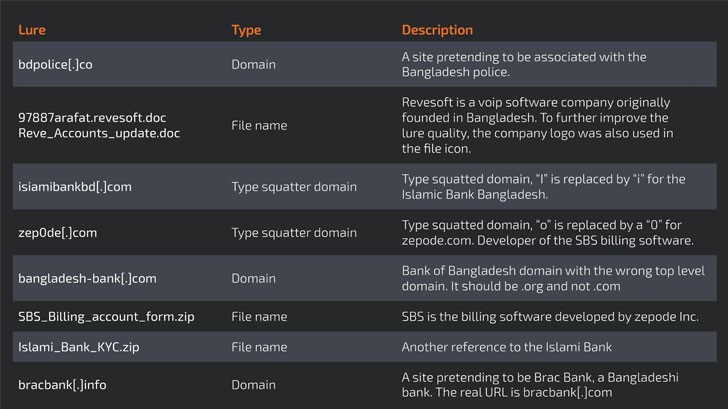
The Android variant of the malware can click photographs and capture screenshots, read call logs and SMSs, send SMS and perform calls to particular numbers, and block SMS messages or calls. Its most recent Windows counterpart comes with new commands that support remote access to the selected machine through Remote Desktop Protocol (RDP) and the Sound command that utilizes the BASS sound library to collect sound from the associated microphone.
Researchers from Cisco Talos said that “The fact that the threat group has evolved into hybrid campaigns targeting Windows and Android shows a group that is thriving and evolving.”
“Along with these improvements, the threat actor has now focused on specific targets, indicating more mature operational capabilities. As is the case with earlier versions of Loda, both versions of this new iteration pose a serious threat, as they can lead to a significant data breach or heavy financial loss,” researchers continued.
Researchers concluded explaining that, “The threat actor behind Loda is diversifying its target platforms and continuously improving functionality. Along with these improvements, the threat actor has now focused on specific targets, indicating more mature operational capabilities. As is the case with earlier versions of Loda, both versions of this new iteration pose a serious threat, as they can lead to a significant data breach or heavy financial loss. The group has decided to deploy a cross-platform malware with some additional capabilities, suggesting they have their eyes on targeting larger organizations over time. As always we encourage users to be vigilant when they’re clicking on or opening any links via email or SMS message. This actor has made use of squatted domains to try and preserve some legitimacy however, as detailed, these are made to look familiar to the real domains to try and lure the user in without noticing.”
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.




