Malware For Apple M1 Chip Has Been Discovered For The First Time In The Wild

The first malware variant custom-fitted to run locally on Apple’s M1 chips has been found, hinting another advancement that demonstrates that threat actors have started adjusting with vindictive software to focus on the organization’s most recent generation of Macs fueled by its own processors.
While the transition to Apple silicon has required developers to construct new variants of their applications to guarantee better compatibility and performance, malware creators are currently attempting comparable strides to assemble malware that is fit for executing locally on Apple’s new M1 frameworks, as indicated by macOS Security specialist Patrick Wardle.
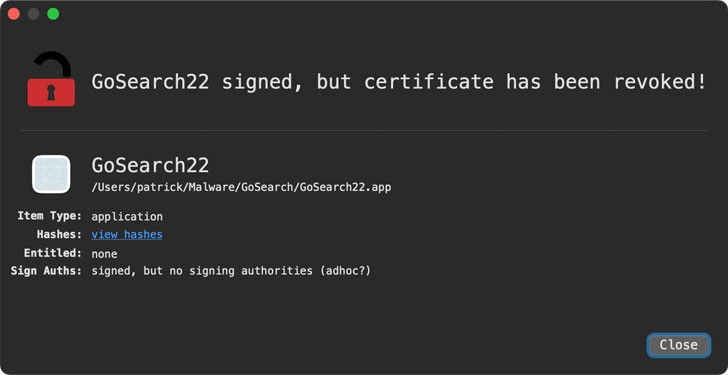
Wardle explains a Safari adware extension known as GoSearch22 which was initially composed to run on Intel x86 chips however it has since been ported to run on ARM-based M1 chips. The malicious extension, which is a variation of the Pirrit promoting malware, was first found in the wild on November 23, 2020, as indicated by an example published on VirusTotal on December 27.
Wardle in a blog post yesterday, said that “Today we confirmed that malicious adversaries are indeed crafting multi-architecture applications so that their code will natively run on M1 systems. The malicious GoSearch22 application may be the first example of such natively M1 compatible code.”
M1 Macs are capable of running x86 software with the assistance of a powerful binary interpreter/translator called Rosetta, the advantages of local help mean proficiency upgrades as well as the improved probability of remaining under the radar without drawing in any undesirable attention.
Pirrit was first reported in 2016 and is a tenacious Mac adware family infamous for forcing intrusive and tricky ads to clients which when clicked, downloads and introduces undesirable applications that accompany features of collecting data.
The intensely jumbled GoSearch22 adware masks itself as a genuine extension for Safari browser, it gathers browsing information and prompts countless advertisements, for example, popups and banners, including some that connect to doubting sites to further distribute additional malware.
Wardle said that the extension was signed with an Apple Developer ID “hongsheng_yan” in November to hide its noxious content details further, yet it has since been disavowed, which means that the application will not, at this point run on macOS except if assailants re-sign it with another certificate.
Albeit the advancement features how malware keeps on developing in direct reaction to both equipment changes, Wardle cautioned that tools for static investigation or antivirus motors may battle with arm64 binaries, with recognitions from industry driving security software dropping by 15% when compared with the Intel x86_64 variants.
GoSearch22’s malware abilities may not be totally new or hazardous, however, that is irrelevant. Regardless, the development of new M1-viable malware signals this is only a beginning, and more variations are probably going to manifest later on.
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.




