Researchers Found Pakistan Officials Being Targeted By New Android Spying Campaign

Researchers from Lookout discovered two new Android surveillanceware families that have been targeting military, nuclear/atomic, and political entities of Pakistan and Kashmir as a component of a pro-India, which is a nation-backed/state-sponsored hacking operation/campaign.
The malwares named Hornbill and Sunbird imitate genuine or apparently harmless administrations to cover its tracks, just to subtly gather SMSs, encoded content of messaging applications, and geolocation, among different sorts of confidential data.
The discoveries distributed by Lookout are the aftereffect of an examination of 18GB of extracted data that was openly available from six improperly arranged and misconfigured command-and-control (C2) servers situated in India.
The researchers from Lookout, in a blog post, said that “Some notable targets included an individual who applied for a position at the Pakistan Atomic Energy Commission, individuals with numerous contacts in the Pakistan Air Force (PAF), as well as officers responsible for electoral rolls (Booth Level Officers) located in the Pulwama district of Kashmir.”
This cyber-espionage attack was focused on 156 casualties with phone numbers from India, Pakistan, and Kazakhstan for a very long period of time, i.e. several years.
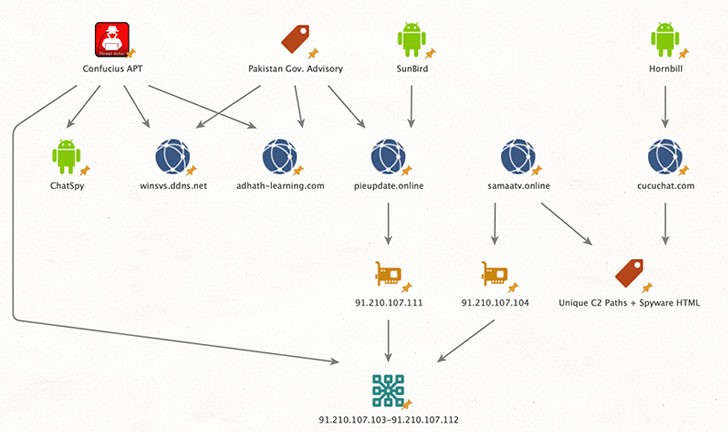
The two malwares/tools utilized in these attacks are linked to an APT (Advanced Persistent Threats) who is known as Confucius. It is a gathering known for its assaults on South Asian nations since 2013. The cybersecurity organization considered Hornbill as a passive reconnaissance tool.
Hornbill has all the earmarks of being gotten from a similar code base as a formerly dynamic business observation product known as MobileSpy and SunBird has been linked to a group of Indian developers responsible for another mobile tracking software known as BuzzOut. Hints of information revealed by Lookout likewise highlight the reality that the administrators of Hornbill cooperated with different Android and iOS application development companies enlisted and working in or close to the Indian city of Chandigarh.
Both the malicious spywares are prepared to gather a wide scope of information, including contacts, call logs, system data, geolocation, photographs that are stored on external drives, capturing sound and video, extracting screenshots, and specific attention on looting WhatsApp messages and voice notes by manhandling Android’s accessibility APIs.
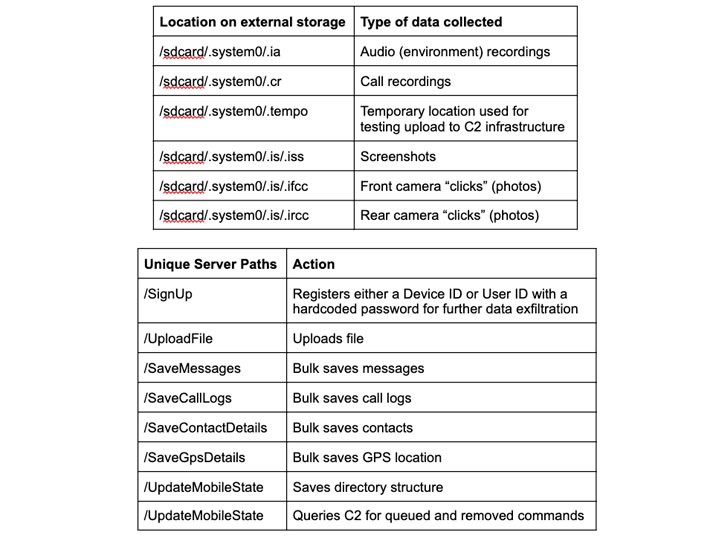
SunBird likewise varies from Hornbill as it incorporates services like remote access Trojan (RAT) usefulness which permits the attackers to execute malicious commands on the targeted and infected device. Likewise, it is also capable of exfiltrating the history of the browser, schedule data, and in some cases, siphoning data from BlackBerry Messenger and IMO texting applications.
Researchers highlighted that “Samples of SunBird have been found hosted on third-party app stores, indicating one possible distribution mechanism,” the researchers detailed. “Considering many of these malware samples are trojanized, as in they contain complete user functionality, social engineering may also play a part in convincing targets to install the malware.”
Researchers of Lookout distinguished Hornbill samples as of late as December 2020, showing an active utilization of the malware since their disclosure in 2018. Then again, Sunbird appears to have been effectively & actively distributed in 2018 and 2019, prior to the bad actor shifting to a different Android-based spyware software, a year ago, called ChatSpy.
Strangely, the command-and-control framework shared by Hornbill and SunBird uncovers further associations with other stalkerware campaigns led by the Confucius group, including an openly available 2018 Pakistani government warning about a desktop malware crusade focusing on officials and government staff, hinting that the two malwares/tools are utilized by a similar threat actor for various reconnaissance purposes.
Despite the fact that India has been a moderately new contestant in the spyware and reconnaissance area, Citizen Lab analysts in June 2020 unveiled a hack-for-hire group situated in Delhi considered BellTroX InfoTech that was aimed to steal credentials from journalists, support gatherings, venture firms, and a variety of other prominent targets.
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.


