Iran Performing Espionage Campaigns On Dissidents

As per CheckPoint, a cybersecurity company, over 1000 dissidents and expats are being targeted by two separate surveillance campaigns being operated in cyber-space by Iran.
CheckPoint researchers explained that the campaigns were initiated against people in Iran and other 12 different nations involving the US and UK. Also, the two groups behind the campaigns were utilizing new procedures to install spyware on the targeted PCs and mobile phones. What’s more, this was, at the time, being utilized to capture call recordings and files of media.
One of these two cybercrime group is known as Domestic Kitten or APT-50 and is charged for fooling individuals to download malevolent software on mobile phones by an assortment of means including the repackaging of a current variant of a genuine video game available on the Google Play store, mirroring an application of restaurant in Tehran, serving/distributing a fake mobile-security application, distributing a compromised application that publishes articles from a local news organization, providing a tainted wallpaper application containing pro-Islamic State imagery, and taking on the appearance of an Android application store to download and install further software.
The campaign is being considered to target 1,200 casualties living in seven nations, as reported by the researchers of the American-Israeli organization. It also said that over 600 infections have been successful.
The second cybercrime group is known as Infy or Prince Of Persia and is said to keep an eye on the home and work PCs of protesters/dissidents in 12 nations and extract confidential information after fooling individuals into opening pernicious attachments of emails. The Iranian government has not remarked on the report.
Operations and activities of the Domestic Kitten were first recognized in 2018. Furthermore, CheckPoint explained that there was proof of it running at least 10 campaigns since 2017. Four of these campaigns were as yet active till the beginning of November 2020.
Also, it was utilizing an Iranian blog webpage, Telegram channels, and instant text messages to bait individuals into installing its tainted software, which the specialists have named Furball, and is capable of recording calls and different sounds, tracking the gadget’s location, gathering device identifiers, collect instant messages and call logs, steal media files including photos and videos, acquiring a rundown of other downloaded and installed applications and stealing files from the external storage.
The 600 infections which were successful are considered to have included dissidents, protesters, opposition forces, and individuals having a place with the Kurdish ethnic minority in countries including Iran, Pakistan, Afghanistan, Uzbekistan, Turkey, Great Britain, and the US. The second group, Infy, is believed to be working since 2007.
The research said that its latest action had focused on PCs, with counterfeit emails with appealing content, generally using an attached document. One instance provided was a record clearly about loans being offered to handicapped veterans. When the file or document was opened, a spying instrument was installed and confidential information was stolen.
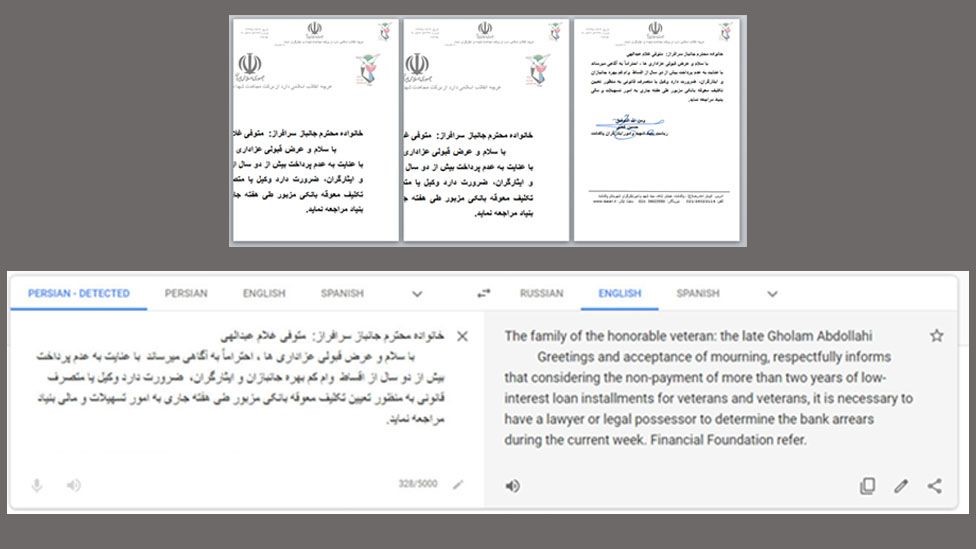
Two reports as of late utilized are said to have incorporated a photograph of an Iranian governor with suspected contact details.
The specialists said Infy’s capacities were far superior to most other realized Iranian missions, on account of its capacity to be exceptionally particular about its targets and to have gone undetected.
Yaniv Balmas, the head of CheckPoint cyber research, said that “It is clear that the Iranian government is investing significant resources into cyber-operations. The operators of these Iranian cyber-espionage campaigns seem to be completely unaffected by any counter-activities done by others, even though both campaigns had been revealed and even stopped in the past. They have simply restarted.”
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.


