Researcher Demonstrate Hacking of 3D Printer by Triggering a Fire
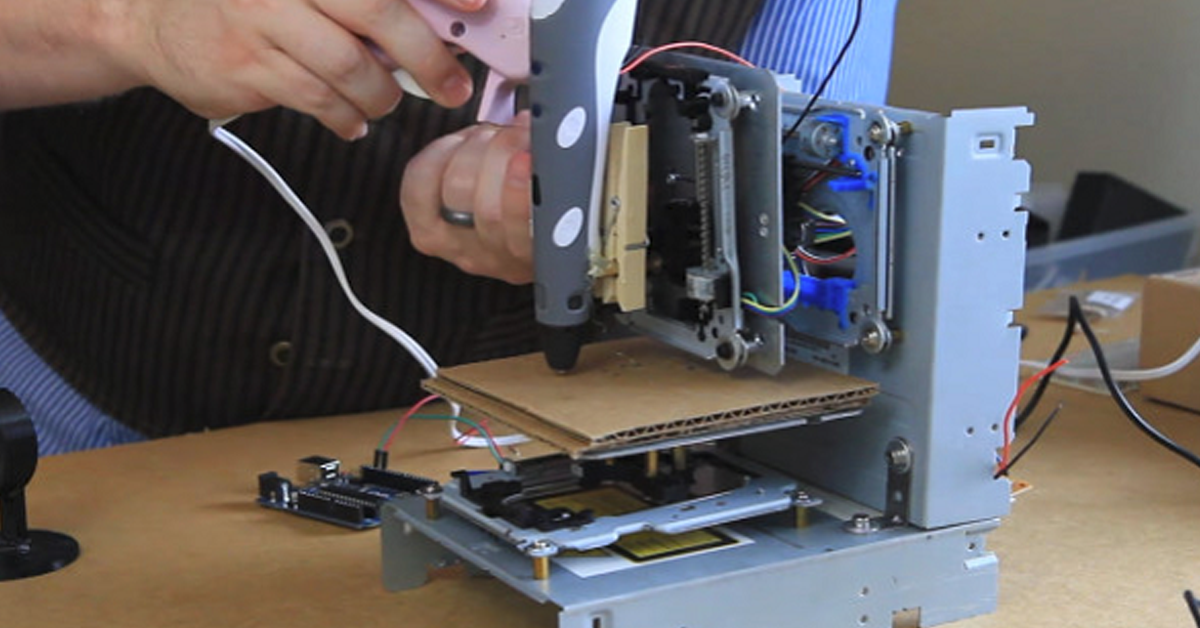
A senior security consultant at Coalfire, Dan McInerney, published a three-part blog where he talks about the threats that modern-day IoT devices pose through an experiment. The experiment exposes the possibility of physical harm that the exploitation of these devices can cause even remotely. Such devices contain heating elements that can be weaponized by the attackers for…
Read more














Recent Comments