ReVoLTE: Eavesdropping Possible on Encrypted LTE Calls

A new study revealed a foundational vulnerability in the VoLTE calls, which could enable the attacker to eavesdrop on voice calls and even extract important data. The vulnerability is named ReVoLTE. The study Call Me Maybe is conducted by researchers from Ruhr University Bochum.
A theoretical framework for the study was laid down by Raza and Lu in a report earlier. They presented that by jamming particular messages and reinstalling a key, theoretically, ReVoLTE was feasible. But the present research focuses on the real-life application of the attack. The same attack vector was found by the researchers in the upcoming 5G network.
How the attack works
The VoLTE specification allows using the packet-based LTE network and IP protocols to establish voice and media calls.
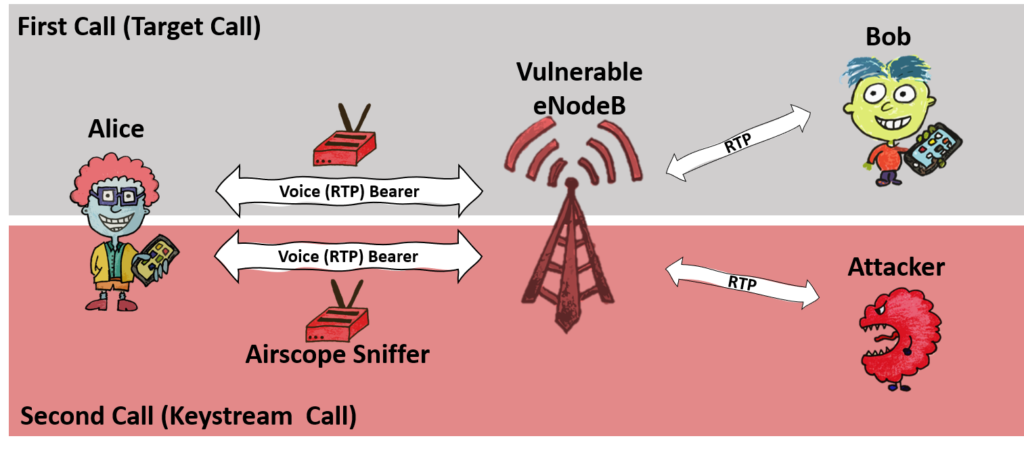
ReVoLTE is a two-layer attack that allows the user to reuse Encrypted VoLTE traffic. Keystream reuse is exploited for carrying out the attack. When a second call is made over the same radio connection as the first one, the first call’s packets are encrypted with the same keystream as the packets of the second call.
The victim’s User Equipment (such as a mobile phone) establishes a connection with eNodeB in its radio cell, and a dedicated bearer with an encrypted key is generated. The attacker places down a link sniffer in the same radio cell to monitor the target cell. He/she then makes the keystream call. The second call requires a dedicated bearer, but since the call happens immediately after the first call and is formed over the same radio cell, it lets the encrypted key to set up the same as the first call.
After generating a sufficient amount of data, the attacker cancels the call. The obtained data is then used to decrypt the packets of the first call, and hence the eavesdropping attack becomes a success.
The researchers revealed that the attackers could execute the attack using equipment of up to $7000.
Randomly selected base stations around Germany were picked for the purpose of the study. Researchers revealed that they found 80% of users exposed to the attack. GSMA was informed about the vulnerability in December 2019, and it issued updates to address the issue.
Increasing bearer identities was recommended as a small term defense method. As a long term defense mechanism, researchers suggested specifying mandatory media encryption and integrity protection for VoLTE.
The German operators have fixed the issue, but many operators are still vulnerable to the attack. For checking if they are vulnerable, the researchers had launched an app. The app is available open-source and can be downloaded from GitHub.
The research team has also made a dedicated website, especially for ReVoLTE. The website is named the same as the paper ‘Call me maybe.’
VoLTE promises low call-setup times and high-definition voice quality while being seamlessly integrated into the standard call procedure. Due to this widespread use, successful attacks against VoLTE can affect a large number of users worldwide, and they may not have the slightest idea about their vulnerability.
Do you like this article? Follow TheHackReport on Facebook, Twitter and LinkedIn to read more exclusive content we post.


