EVILNUM group targeting Financial firm

EVILNUM, an advanced and persistent threat community with the bulk of targets in EU countries and the United Kingdom, has also noticed threats in countries such as Australia and Canada. According to ESET’s telemetry, the EVILNUM group’s priorities are financial technology firms – for example, businesses that provide online exchange services and resources.
Previously, Evilnum ‘s malicious operations are conducted using malware scripts written in commonly used programming languages such as C # and JavaScript. Based on the latest findings from Cybereason, a US-based cybersecurity company, Evilnum is also now utilizing Python-scripted remote access trojans (RATs) that have recently been uncovered along with a range of other targeted attacks.
EVILNUM malware was the first variant detected and published in 2018. Palo Alto published the second edition, targeting a finance technology company (FinTech).
Evilnum’s toolset has evolved in recent years and now contains custom malware — including the Evilnum malware family — and hacking software bought from Golden chickens. According to the ESET company, Malware-as-a-Service (MaaS) provider, which also contains FIN6 and Cobalt Company among its customers.
SNAPSHOT of the Attack
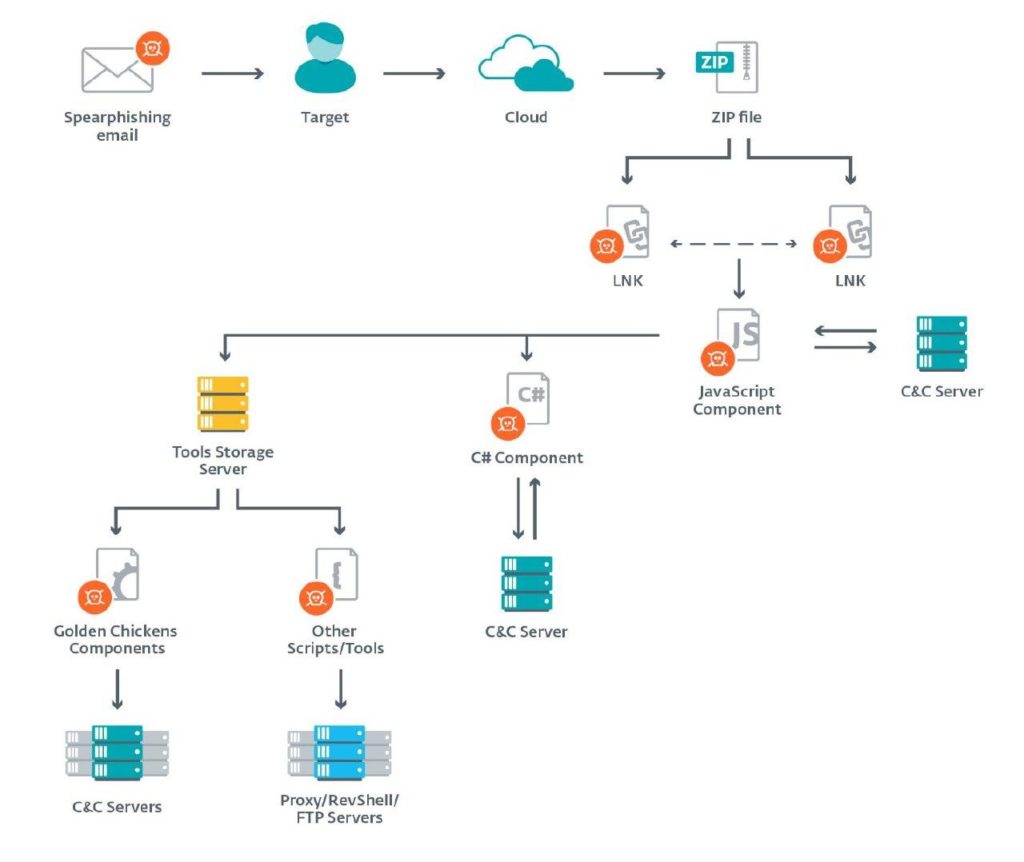
Targets are being attacked with spear phishing emails, and this agent has been delivered from a URL on a cloud-platform that contains a link to a ZIP file hosted on Google Drive. This folder contains many LNK files or shortcuts that extract and execute a malicious JavaScript portion while viewing a decoy text. These shortcut files have “double extensions” to try to deceive the user into opening them, assuming they are harmless documents or images.
When the link is opened, the user installs a compressed folder loaded with trojanized files (using copies of a driving license or bills with proof of address) that masquerades as PDFs and JPEGs. These files present themselves to the end-user as obviously harmless decoys, all while running silently in the background. This decoy documents tend to be genuine and have been compiled by the group over many years of operation.
The JavaScript framework is the first stage of the attack and can deploy other malware, such as a C # spy frame, Golden Chickens components, or Python-based applications. Some researchers in the past gave the name Evilnum to the C # component, but the JS component was often referred to as Evilnum. Each of the modules has its own C&C server, and each system works separately.
The malware operators manually send commands to install additional components and use post-compromise scripts and software where they find it appropriate. This component achieves persistence via the Run registry key and has complete backdoor capabilities: it can download and execute binaries, run arbitrary commands or upload files to the C&C server from the victim’s computer.
The key aim of the EVILNUM Community is to spy on its targets and to collect financial information from both the target firms and their clients such as Customer lists, savings and business activities spreadsheets and records, Software licenses and credentials, Sensitive information like Cookies and session details, Email credential, Customer’s credit card records and verification of address/identity documentation.
EVILNUM group has been aimed at the finance industry since 2018 and has found popularity because of their willingness to use creative approaches to keep ahead of protective steps, such as using JavaScript-based agents rather than focusing on more widely used methods such as executable files. They continued to refine this agent by altering certain files’ location to prevent detection by certain antivirus software and adjusting contact habits while those devices are being used. To bypass detection, they created an intricate command and control retrieval strategy by embedding instructions for using well-known platforms. They have programmed the agent to use multiple C2 nodes, based on the protection items the host computer requires.
One way to defend against this hazard is to uninstall shortcut files from Microsoft on high-risk devices that communicate with untrusted parties daily. These high-risk computers can also be segmented within the network to discourage attackers from laterally spreading once they have been infected. To search for suspicious links to the IP addresses connected with virtual private servers, we suggest regularly checking network logs.
Do you like this article? Follow TheHackReport on Facebook, Twitter and LinkedIn to read more exclusive content we post.


