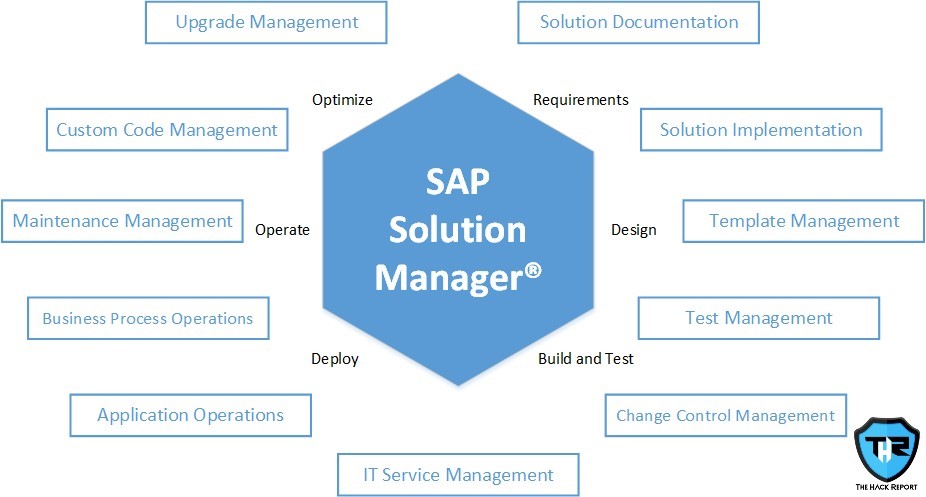
Any Unprivileged User Can Gain Root Privileges On A Linux System Using A Default Sudo Configuration
The research team of Qualys, recently found a vulnerability in sudo, dubbed as the heap overflow vulnerability. Sudo is an omnipresent and powerful open-source utility that is mainly utilized on operating systems like Unix and Linux. This vulnerability has been registered as CVE-2021-3156. Exploiting this vulnerability can allow any unauthorized user, without any permissions, to…
Read more











Recent Comments