What is Open Source Intelligence (OSINT)- How can I make use of it?
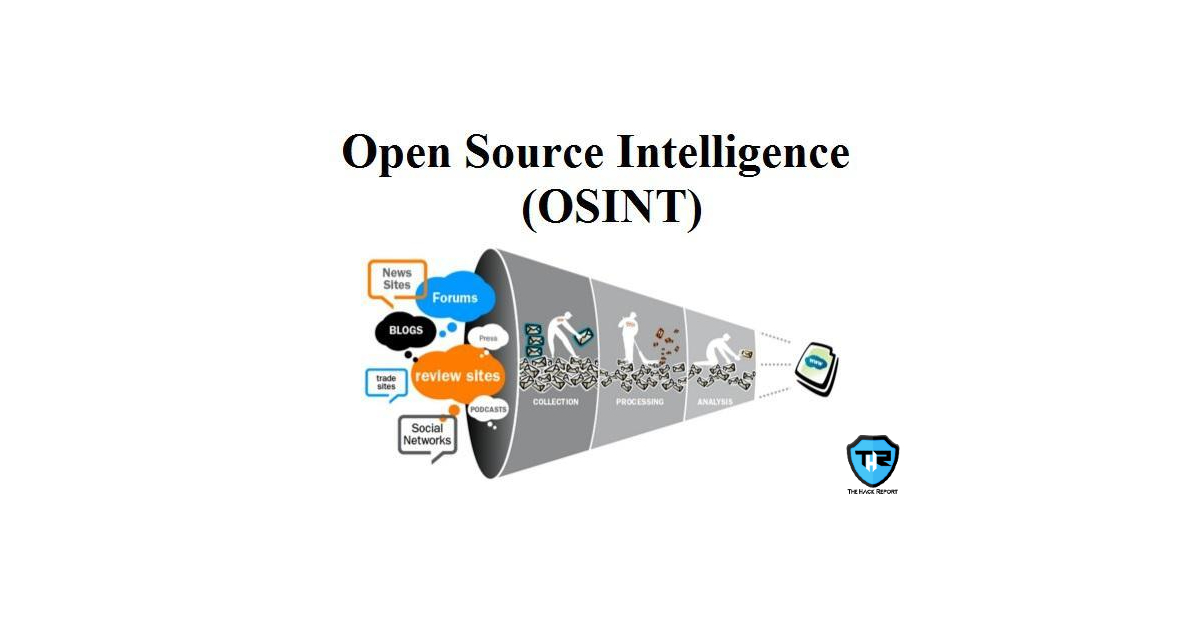
OSINT represents Open Source Intelligence and it is one of the key viewpoints in understanding the cybersecurity awareness that leads the Internet nowadays. The term OSINT
originates from numerous many years prior. Indeed, US military offices began utilizing the term OSINT in the last part of the 1980s as they were re-examining the idea of data prerequisites in strategic levels under war zones. At that point in 1992, the Intelligence Reorganization Act specified the core objectives of intelligence collection, which included central principles. Must be target knowledge liberated from inclination Information must be accessible on open and non-public sources.
Open-source knowledge (OSINT) is data gathered from public sources, for example, those accessible on the Internet. Although the term isn’t carefully restricted to the web but instead implies all freely accessible sources. “OS” (from OSINT) implies Open Source. For this situation, it is not linked to the popular open-source campaign, but a freely accessible source where information can be accessed by the user in their compilation of intelligence data.
Information is the keyword behind the concept of OSINT, and, most importantly, information that can be obtained free of charge. If it is public, free, and legal, it does not matter whether it is located inside journals, blogs, websites, tweets, social media cards, photos, podcasts, or videos.
How OSINT Used in Cybersecurity?
Organizations and people use OSINT throughout the day, as we’ve appeared previously, but then they don’t deliberately have any acquaintance with it.
OSINT is often used by Sales, Marketing, and Product Management departments to maximize conversions. To be more precise, while supplying the public with their services.
Using the right utilities for your OSINT investigation will be very powerful in the cybersecurity sector if you pair it with strategic thought and have a consistent OSINT approach. Regardless of whether you are running a cybersecurity investigation against an organization/individual or whether you are operating on the other side to detect and prevent potential risks, having pre-characterized OSINT strategies and clear objectives can spare you a great deal of time.
Most IT organizations don’t grasp OSINT to support their network protection guards. This may turn into an issue as they are unable to recognize and track vulnerabilities to software, utilities, and/or cybersecurity.
OSINT Strategies
OSINT strategies can be isolated into Active and Passive strategies, with active tactics involving any form of real interaction with the target and passive tactics preventing some interaction with the target. Aggressive approaches often entail a slight chance of the target detecting that you are researching them. Whereas passive strategies typically involve querying someone else ‘s managed database, which typically does not involve the chance of being identified.
A functioning OSINT strategy could be as basic as checking a site and web server or registering to download the product catalog of a rival. Although this minor interaction obviously won’t blow your inquiry, matching a download to the IP address of your company might tip off a topic being investigated by your company. Comparatively, a proactive approach such as using a search engine such as Shodan to review a company’s resources without searching them yourself will be almost difficult.
Risks of conducting an OSINT investigation
When we spoke about active/passive tactics, we touched on the dangers of carrying out an OSINT investigation, but it is important to highlight the issue. It is one of the fields of OSINT study that is most often ignored.
- Risk of detection: This concerns the direct contact made using active techniques or services from third parties that may give you away as the searcher.
- Risk of losing access to sensitive content: Once they realize you’re following their means or searching for their data, they can begin eradicating their own path and shut down open information from interpersonal organizations, profiles, and so forth.
- Risk of being the victim: Danger of turning into the person in question: After everything, you can wind up being the objective of an examination, or far and away more terrible, the association you have a place with can endure that destiny. Extraordinary consideration ought to be taken when utilizing OSINT strategies.





One Response
[…] Lohar, a security researcher for The Hacker Report, recently wrote an article exploring the concept of open source intelligence, including its definition, use cases and […]