Pre-Valentine Malware Attack Using Phishing Emails To Imposter Well-Known Lingerie & Flower Stores

As Valentine’s Day approaches at the end of this week, a lot of people have recently received order confirmation emails for lingerie and flowers. But actually, these confirmation emails are a part of a spear-phishing assault that will eventually drive casualties to a noxious document or file that will execute the BazaLoader malware.
The BazaLoader downloader is written in C++ and has the essential capacity of downloading and executing extra modules. BazaLoader was first seen in the wild in April 2020 and from that point onwards specialists and observers have seen a minimum of six different versions indicating dynamic and constant improvements in the malware. As of late, specialists found numerous BazaLoader crusades in January and February which depended intensely on human interaction with various websites, email lures, and attachments of PDF.
Researchers from Proofpoint, in a blog post, said that they “have spotted multiple BazaLoader campaigns in January and February 2021 involving the tactic of heavily relying on human interaction with different sites, PDF attachments, and email lures. There was a range of lure and subject topics, including compact storage devices, office supplies, pharmaceutical supplies, and sports nutrition, but what stuck out were campaigns that were timely and relevant to the upcoming Valentine’s Day holiday. The campaigns were spread across a diverse set of companies and sectors.”
One of these emails claimed to be from Ajour Lingerie, which is a great, high-quality, online lingerie shop based out of New York. The email claimed that the casualty has finished the request and should check the receipt and confirm the cost of their purchase.
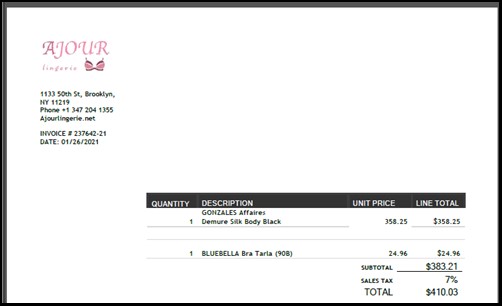
The affixed PDF remarked as invoice_NI52224162K.pdf was found to be not malevolent. It rather references a particular client order number and purchased product related to it. In one such instance, the order aggregated $410.03 which could send the casualty into a state of frenzy.
The receipt received by casualties likewise had a link to a website claiming to be of Ajour Lingerie. Be that as it may, the website, ajourlingerie.net, is not quite the same as the genuine site for Ajour Lingerie, which is ajour.com.
Attackers broadly expounded to make the malicious and fake Ajour Lingerie site look genuine including details from the logo to the location.
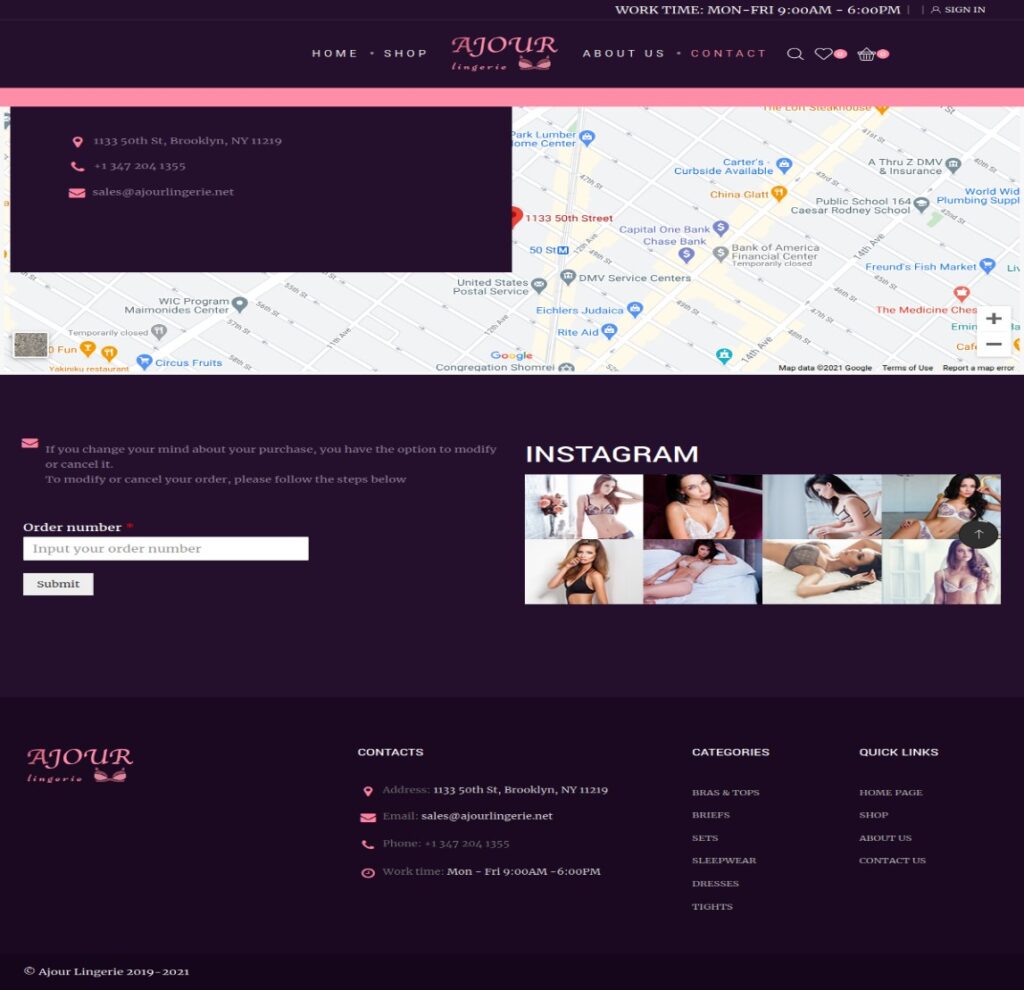
Researchers explained that “The websites the user would browse to are fake, but the actors took care to have the physical addresses match a near-legitimate location. For instance, Ajour Lingerie is not located at 1133 50th St, Brooklyn, NY 11219, but this address is in physical proximity to a legitimate website and physical business called the Lingerie Shop.”
The site additionally had a “contact” page which was actually the malicious one. In the event that clients visited this page, they were then given the choice to enter the order number in the request ID. The contact page at that point directs them to the malicious page, which was connected to an Excel sheet. This Excel sheet contained macros that whenever enabled or initiated by the client, would download BazaLoader.
Another subsequent email utilized a nearly indistinguishable technique except, this time, implying to be from Rose World. This email similarly references a request from Rose World’s online store and has a PDF affixed delineating the order, in an instance the total being $104.58, with references to purchases of flowers at the fake Rose World site, roseworld.shop.
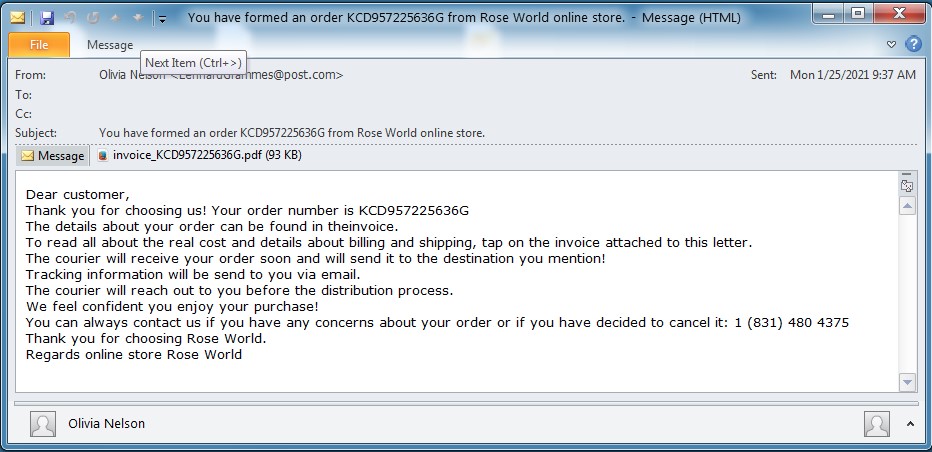
“This campaign is nearly identical—enticing users to check an order number. The campaign delivered PDF attachments with references to purchases at the Rose World website. If the user visits the website, navigates to “Contact Us”, and enters the order number in the order ID, the site will redirect the user to a landing page. This landing page links to and explains how to open the Excel sheet. The Excel sheet contains macros that, if enabled, will download BazaLoader,” researchers explained.
However, researchers didn’t determine what malware gets downloaded subsequent to this first-stage contamination. BazaLoader has been known for its code being similar to TrickBot and has been related to Ryuk ransomware.
Scientists cautioned that they have noticed a consistent development in attackers utilizing BazaLoader as a first-stage downloader. This increase or escalation in BazaLoader spreading has been running simultaneously with the advancement of the loader especially during the long stretch of October 2020. The latest Valentine’s Day assault strikingly mirrors an assault vector with an elevation in human interaction.
The utilization of such techniques is the display of intelligence of cybercriminals horning in on Valentine’s Day, which has remained a mainstream phishing subject over the previous years. Last February, a pernicious email crusade focused on iPhone proprietors attempted to persuade them to download a phony dating application. Furthermore, in 2018, scientists cautioned that Necurs botnet action was spiking as scammers utilized the network to flood inboxes with guarantees of friendship, in a piece of an occasional rush of Valentine’s Day-themed spam.
“These recent BazaLoader campaigns exemplify affiliate actors leveraging a loader that is increasingly popular and more reliant on human interaction. Further, the social engineering features rely on the timeliness of the Valentine’s Day holiday and the intrinsic user curiosity to see what they may have ordered,” researchers concluded.
“Valentine’s Day, while not abused to the level of other holidays, presents an opportunity for a variety of actors. The FBI Boston field office has posted public warnings of romance scams. While this is not a romance scam, it is an example of social engineering, well-timed with the Valentine’s Day holiday.”
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.


