Preventing Risks From Subdomain Takeover – Cloud Exploits
33 billion records were leaked in 2018 and 2019 because of inappropriate cloud security. Since 2019, an expansion of more than 300% in the number of penetration tests performed against cloud environments. During cloud penetration tests, configuration errors are regularly discovered which could prompt significant issues, for instance, misconfigured openly visible AWS S3 storage buckets. It is assessed that cloud misconfigurations cost organizations all around the globe, almost $5 trillion just in 2018 and 2019 alone.
Misconfigurations are a broadly known cloud vulnerability classification, subdomain takeovers which is an especially extreme issue are a zone that is usually seen during cloud-centered penetration tests. Cloud framework permits organizations to rapidly transmit environments and tear them down when not needed. Notwithstanding, when organizations are done they frequently ignore eliminating the domain name system (DNS) configured during the arrangement (known as leaving a dangling pointer). This slip-up could result in unwittingly facilitating malware and phishing websites. Phishing operations that take control over sites inside the domain of the organization are less dubious and clients and workers are bound to fall prey to these assaults. When an assailant is in control of a subdomain, they can acquire chain-of-trust validity past web resources bringing about clients or workers signing into an attacker-owned framework. The reputational harm from a break like this could be colossal and bring about loss of income and costs from lawsuits.
While numerous conditions incorporate DNS names for objects, the actual names are typically important for the cloud supplier’s domain. Development groups will make false names utilizing their own domain for a superior and better trusting client experience. For instance, when organizations dispatch new miniature sites as a feature of promoting and brand crusades, the site is accessed through a content delivery network (CDN) in the cloud to guarantee a quick reaction and great client experience. To keep a strong client experience the organization will make their own pseudonym, for example, “campaign.companyname.com”, that focuses on and shrouds away from the hidden cloud framework.
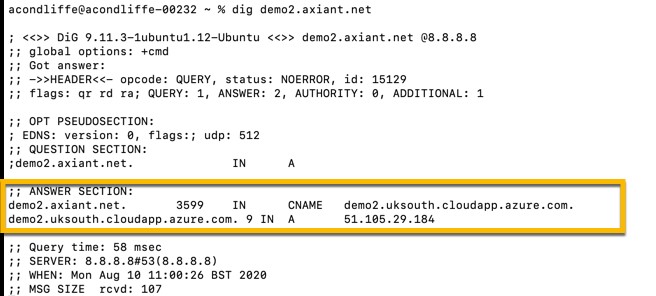
The following is an instance utilizing the “dig” DNS utility. This instance can be utilized to show a test domain that has a cloud service alias. Given below is an illustration of a working alias as exhibited through the “NOERROR” status and has a substantial IP address.
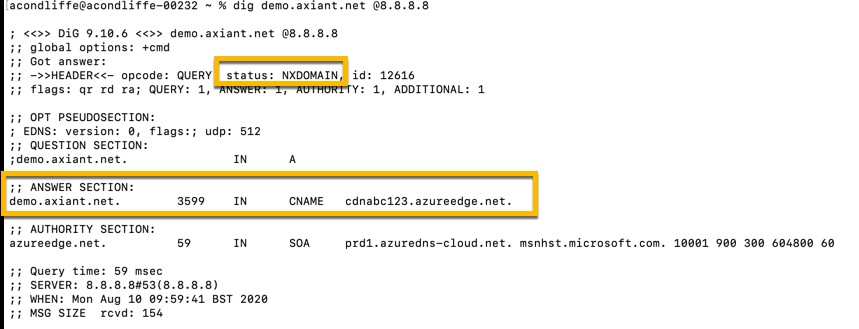
In the second image below, the Microsoft Azure endpoint has been eliminated, yet the DNS data has not been refreshed. The status of the request has changed from “NOERROR” to “NXDOMAIN” on the grounds that the actual endpoint (and the IP addresses related to it) does not exists anymore, however, from the foe’s viewpoint the alias “demo2.axiant.net” is as yet configured.
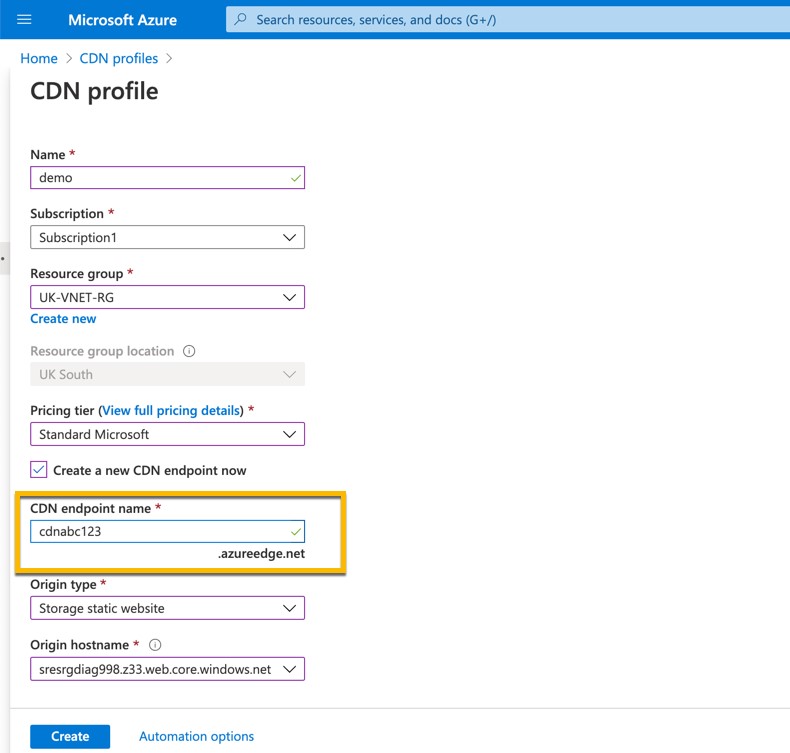
Now an attacker would now be able to make their own endpoint named, “cdnabc123.azureedge.net”. In this example, this is cultivated inside Microsoft’s famous Azure cloud.
At the point when a client visits “demo.axiant.net”, they would now rather be communicating with the server possessed by the bad actor. This permits an attacker to make a phishing effort utilizing a trusted domain name. A phishing effort utilizing a recognizable domain name with a substantial SSL authentication is undeniably persuading and all things considered, clients and representatives would characteristically trust it.
Fortunately remediating this issue isn’t so troublesome. A great practice is to persistently tidy up DNS records particularly, at whatever point, there is a change. You can do this by utilizing your inner security group and a standard DNS automated API-based assistance or by routinely utilizing a service-specified platform to confirm that your cloud resources don’t have any subdomain misconfigurations. Having a normal convention set up for the creation and evacuation of DNS entries, through a mechanized tool lessens the risk of mistakenly ignoring dangling pointers after the environment has been taken out. Subdomain takeovers are not restricted to the Azure cloud, numerous different hosts are powerless to such assaults, for example, S3, WordPress, Zendesk, Github, etc.
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.




