What is Nmap And Why You Should Use It?
IT managers, network administrators, and security experts generally suffer an endless fight, continuously keeping an eye on what precisely is running on their organization’s network and the possible weaknesses/vulnerabilities that hide inside. While there is an abundance of screening/monitoring utilities accessible for network mapping and security reviewing, none can beat Nmap’s blend of flexibility and ease of use, making it a widely recognized and accepted norm.
Nmap stands for Network Mapper and is an open-source and free tool for scanning vulnerabilities and network discovery. Administrators of networks generally utilize Nmap to distinguish what gadgets are running on their frameworks, finding hosts that are accessible and the features they offer, discovering possibly open ports, and also for recognizing security threats.
Nmap can be utilized to screen single hosts and huge networks that envelop a huge number of gadgets, devices, and huge numbers of subnets.
In spite of the fact that Nmap has developed throughout the long term and is amazingly adaptable, on the most fundamental level it’s just a tool for port scanning, gathering data by transmitting raw parcels to ports on the system. It analyzes reactions and decides if ports are open, shut, or filtered somehow or another by, for instance, a firewall. Different terms utilized for scanning ports incorporate port enumeration or discovery.
The packets conveyed by Nmap, get back with IP addresses and an abundance of other information, permitting you to recognize a wide range of attributes of the network, serving you with a map or profile of the network, and permitting you to make an inventory of hardware and software.
Various conventions utilize various sorts of packet structures. Nmap, to transmit error messages, utilizes protocols of transport layer involving TCP (Transmission Control Protocol), UDP (User Datagram Protocol), and SCTP (Stream Control Transmission Protocol), with other supporting conventions like ICMP (Internet Control Message Protocol).
The different conventions are used to fill various needs and ports of the system. For instance, the low asset overhead of UDP is appropriate for constant streaming video, where you compromise some lost packets as a trade-off for speed, while non-continuous real-time streamings on YouTube are supported and utilize the slower, though more dependable TCP.
Alongside its numerous different features, Nmap’s crucial services like port scanning and packet-capture are continually being improved.
Nmap was first presented in Phrack Magazine around September 1997 with its source code and was written in C++. It was later expanded with C, Python, and Perl.
Throughout the long term, Nmap has profited from the contributions from a developing local community of fans and designers, and it presently has been downloaded a huge number of times each day. En route it has accomplished a level of notoriety in mainstream society, turning into the go-to hacking instrument highlighted by directors in at least twelve motion pictures in scenes with stars like Rihanna and Kate Mara.
One of the purposes behind Nmap’s prominence is that it very well may be utilized on a wide range of operating systems such as Windows, macOS, BSD, Solaris, AIX, and AmigaOS, and also supports various Linux variations involving Red Hat, Mandrake, SUSE, and Fedora.
A massive amount of free network monitoring utilities just as free open-source weakness/vulnerability scanners are accessible to security reviewers and network admins. What makes Nmap stand apart as the instrument which IT and network admins require to know is that it is quite adaptable and powerful. The premise of Nmap’s usefulness is the service of scanning ports which it serves for a wide range of related abilities such as:
Network Mapping
Nmap is capable of detecting the gadgets or devices on the network, likewise called host discovery, involving switches, servers, and routers and also about how they’re actually connected.
Operating system detection
Nmap can distinguish the working operating systems on devices or gadgets over the network, likewise called OS fingerprinting, serving the vendor name, the fundamental operating system, the variant of the product, and even a gauge of uptime of the gadget or device.
Service Discovery
Nmap can distinguish hosts over the network and can also determine whether they’re being utilized as mail, web, or name servers, and the specific applications and variants of the related software they’re utilizing.
Security Auditing
Determining what variants of applications and operating systems are being utilized on network hosts permits network managers to decide their weakness/vulnerability to explicit imperfections. In the event that a network administrator gets a caution about a vulnerability in a specific rendition of an application, for instance, one can check their network to distinguish whether that product variant is working on the network and find a way to fix or refresh the significant hosts. Operations like identifying or discovering particular vulnerabilities can be automated by the use of scripts.
Zenmap is the graphical UI of the Nmap security scanner and accommodates many choices. It allows clients to do stuff like saving scans and analyzing them, see maps of network topology, see presentations of ports working on a host on a network, and save checks in an accessible and searchable database.
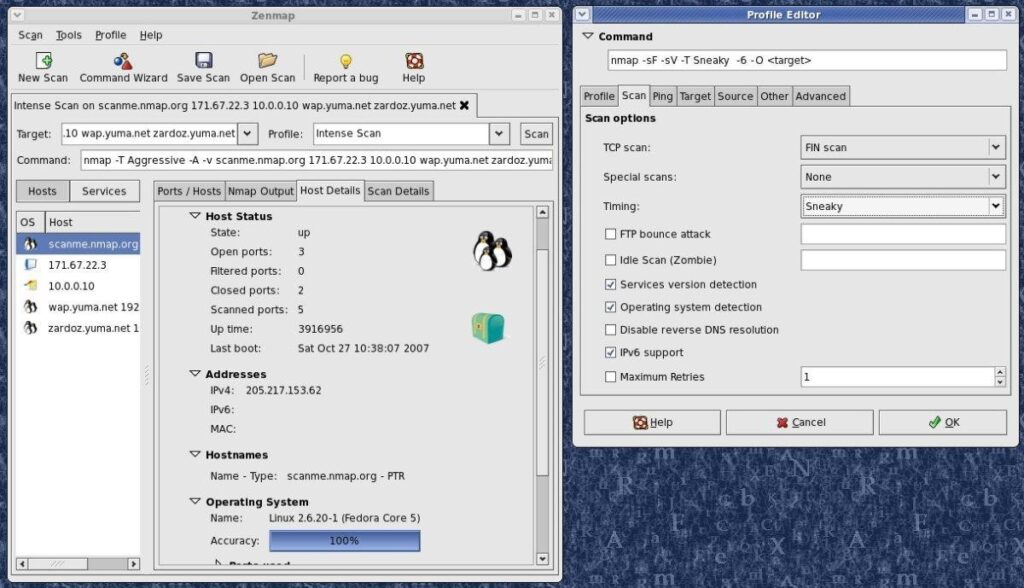
Nmap 7.70 was published/released in March which offered nine new and different NSE scripts and gave many fresh OS and service fingerprints for operating systems and application variant recognition, including fingerprints for IPv6 and IPv4 OS upheld. Improvements in this new variant additionally made recognition of service variants quicker and more precise. As a result of the inescapable utilization of Windows, upgrades to the Npcap Windows packet-capturing library intended to improve execution and steadiness are especially significant.
Scanning of ports as such isn’t unlawful, at any rate under U.S. government law, Nmap’s highlights are absolutely helpful to pernicious hackers testing for vulnerabilities to misuse. Specific employment of the product, particularly without consent, can get you terminated or in lawful difficulty, regardless of whether you’re doing a vulnerability examination for amiable purposes.
Some Nmap filters are genuinely light touch and may not set off alarms, it’s in every case best to get your scannings affirmed with the proper individuals in your organization. Keep in mind that numerous Nmap services like OS fingerprinting, require root advantage.
Installation of Nmap is quite simple yet shifts as per your operating system. Nmap accompanies a custom installer (nmap<version>setup.exe) for Windows. Just download and run the installer and it will automatically install and configure Nmap on your system. On Mac as well, Nmap accompanies a devoted installer. Run the Nmap-<version>mpkg record to begin this installer. On a few new variants of macOS, you may see a caution that Nmap is an unidentified developer, however, you can disregard this admonition. Linux clients have the choice to either compile Nmap from source or utilize their picked package manager. To utilize apt, for example, you can run Nmap, variant to check if Nmap is installed, and sudo apt-get install Nmap to install it.
One of the marvels of Nmap is that beginners with little knowledge of networks or small systems can begin with basic commands for fundamental examining, while experts can use more intricate kinds of tests, which bring about a more fine-grained perspective of the network.
A single command can be utilized to execute a number of common functions and the program itself uses a wide variety of shortcut commands which can be further utilized to automate basic or common operations. Some of the most common commands are:-
Port Scanning
There are a huge number of ways that can be utilized to execute port scanning via Nmap, some of which are mentioned below.

The only difference between all these scans is the fact that do they execute a TCP connection or not and do they include UDP or TCP ports, or not.
Ping Scanning
A ping scan is a scan that serves you with complete information about every active IP over the network and this can be done as follows.

OS Scanning
It is one of the best features of Nmap and when you perform this type of scan, what Nmap does is that it transmits UDP and TCP packets to a specified port and after receiving the response analyzes it with the database including details of 2600 operating systems and then serves you with the data or information regarding the operating system and its version. Use the below-displayed command to perform or execute an OS scan.

Host Scanning
Performing a host scan will serve you further more details and data about a specific range of IP addresses or any specified host and it can be done by using the following command.

Scanning A Number Of Popular Ports
This command could be a lot more useful and helpful if you are using Nmap on a home server as it scans and serves you a rundown of some of the most famous ports. It can be done using the below-displayed command and you can replace the 20 with the number of ports you want to scan.

Output To A File
If you want to output your scan results in a file, all you need to do is, just add an extension to all your commands and it can be easily done as follows.

OR

Disable DNS Name Resolution
Disabling reverse DNS resolution will permit you to increase the speed of your scan in Nmap simply by utilizing the -n parameter. This is much more useful when you want to scan a large or huge network. For instance, to disable DNS resolution for simple ping scan which has been mentioned above, simply add -n.

If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.




