Viewing Cyber Threats Of 2021 Via Cyber Attack Maps

Nowadays, DDoS attacks target a lot of important assets ranging from banks to news sites and offer critical trouble for web clients so that they could not republish and access valuable data. With Cyber Attack Maps anyone can see the DDoS assault parcels occurring between the initial point and destination.
Consequently in the event that you are ignoring a low to fair size Distributed Denial of Service (DDoS) assault, then you should research the information logs and get the data you need to shield yourself from explicit assaults. Despite the fact that, with more critical assaults, manual queries are tedious and very powerless also.
Subsequently, the safeguard needs to have different strategies with the goal that they can battle digital assaults proficiently. Yet, in the event that you are not experiencing a DDoS assault, and need to find out about the top advanced assaults so you can get some information from the cybersecurity clashes taking place around the globe.
Yet, the inquiry emerges as to where one should look about all this data. Basically, one should attempt the Internet Service Provider (ISP) which advices to look at anti-DDOS suppliers. In this way you can perceive what’s happening at the time by watching the cyber assault maps, basically to see and track that from where the cybersecurity works around the world.
In addition, you can likewise witness cyber attacks and how not well-arranged packs interconnect between nations. A cyber attacks map can be utilized to see cyber threats so that one can just watch the grouping of visually advanced threat clashes. Below are some of the Cyber Attack Maps that one can or should utilize for all the above-mentioned purposes:-
Kaspersky Cyberthreat Map
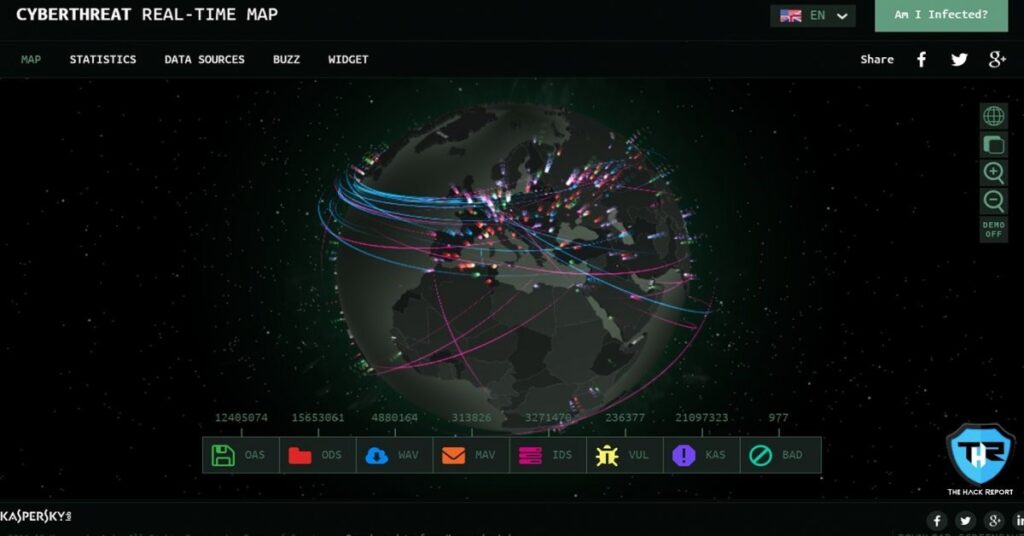
First is the Kaspersky’s Cyberthreat Map which is the biggest cyber attack map out of all the cyber attack/threat maps available all over the web. It is even best in the view of the graphical interface, as it is super smooth and quite detailed with various interactive features. However, this threat map mainly focuses on the factors intended to destroy or damage the web/Internet. Whenever an individual accesses this cyber threat map, it detects the corresponding location and displays various states of your country. In addition, it also displays the biggest social attacks and malwares or viruses that were observed in the previous week. Other than all these features, this cyber threat map constantly performs various live scans and detections that are displayed at the bottom of the page. These scans and detections include On-Access Scan, On-Demand Scan, Intrusion Detection Scan, Vulnerability Scan, Mail Anti-Virus, Web Anti-Virus, Kaspersky Anti-Spam, and Botnet Activity Detection.
Norse Attack Map
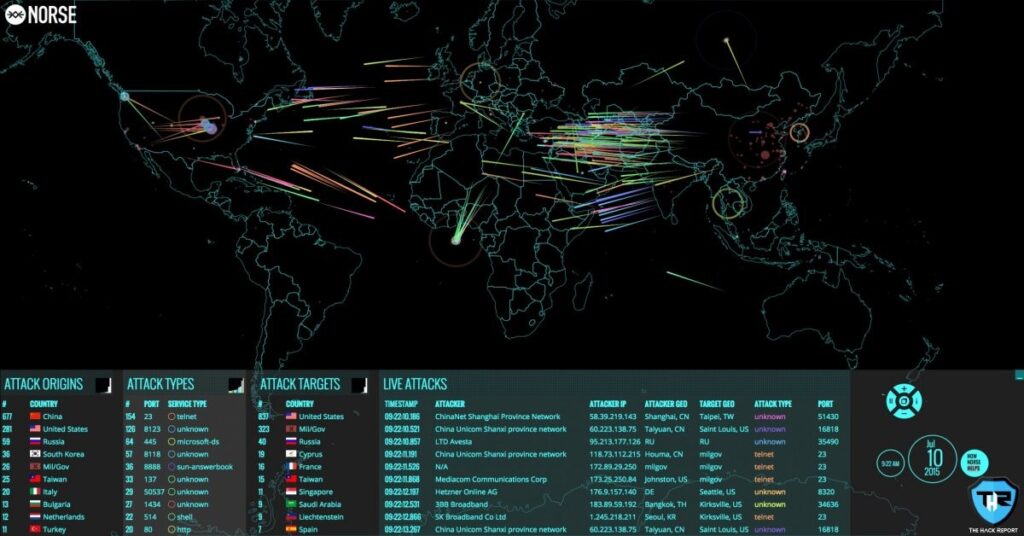
Next comes the Norse Attack map which is also a well-known cyber attack map and is a service of an organization that is a cybersecurity firm and has managed to make its position in the last few years. Norse’s attack map serves anyone with information that includes the origin of the attack with its target, the attack types, and live attack details like timestamp, attacker IP, etc. Keeping in mind the amount of data displayed on this attack map, Norse said that, “based on a small subset of live streams against the Norse honeypot foundation. Interestingly sufficient, companies can add their logo to the map when it is revealed at the office.”
Trend Micro Botnet Map
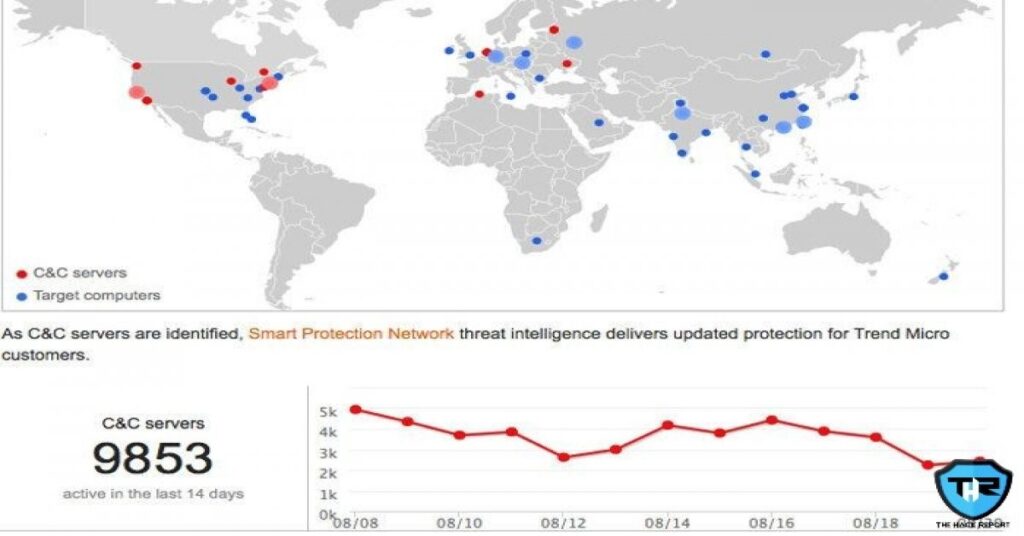
Next is the Trend Micro Botnet Map which is basically a Botnet Connection dashboard and is also a moderate cyber attack map incorporated with just the essential features and services. Being a cyber-attack map and Botnet connection dashboard it tracks and displays command-and-control (C&C or C2) servers that are controlled and managed by the Botnets all around the world. Even though the time duration of the data being displayed is not quite clear and obvious, the traditional data is considered to be there from around 14 days.
DDoS & Cyber Attack Map
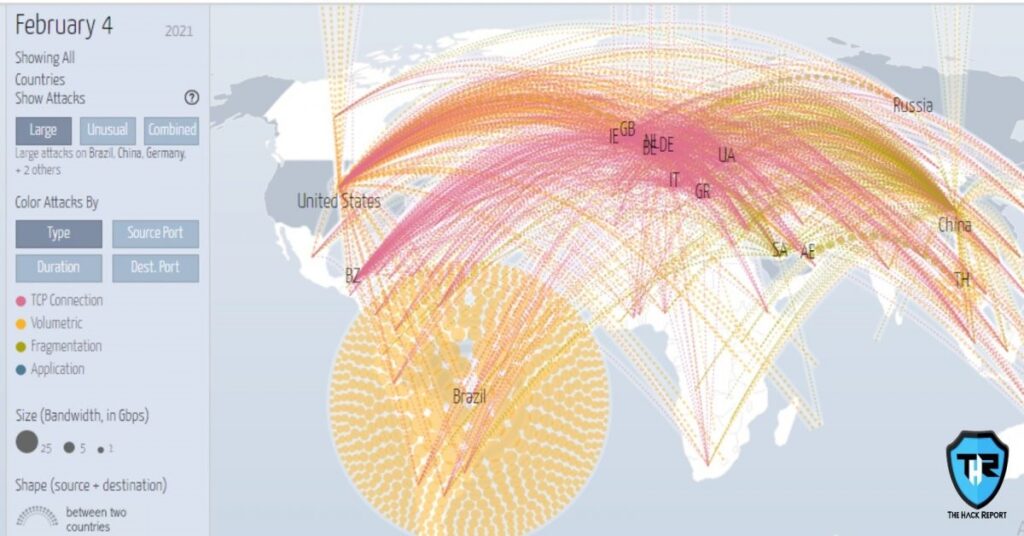
This DDoS & Cyberattack map is a worldwide stage for cybersecurity conditional information. Hence this cyber attack Map applies exceptionally contextualized perceivability inside a complete warning landscape exercise that has been custom fitted for each & every business’s specific geographic and vertical profile. In addition, it utilizes an assortment of tools and techniques to accumulate and analyze the threat information. Accordingly one should unequivocally focus on the capacities and capability of DDoS and digital assaults, basically by choosing different hints of an attack crusade.
FireEye Cyber Threat Map
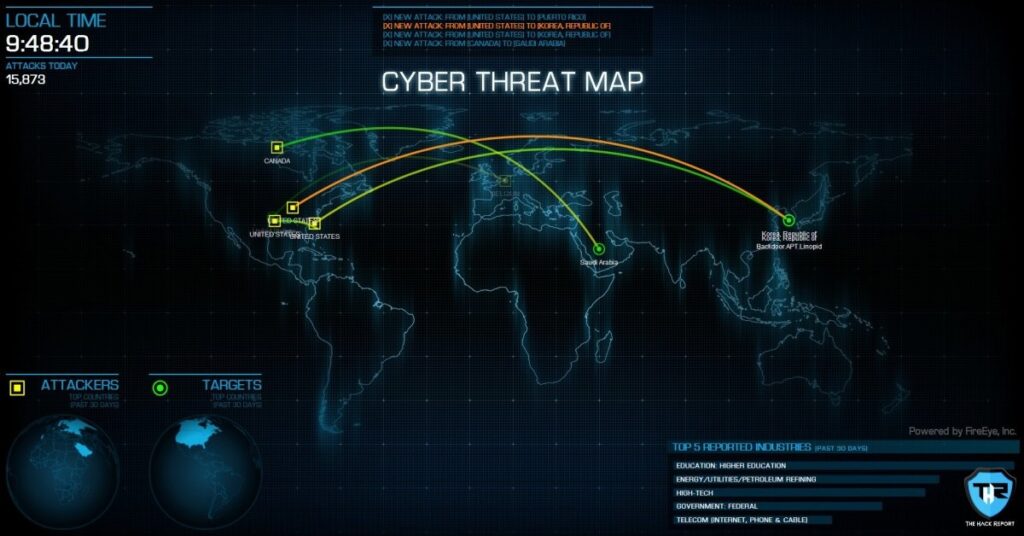
FireEye is another popular and well-known cyber threat map present on the web. This cyber threat map is not at all complex as other above-mentioned maps and could be really helpful if you’re working for the data in industry and country wise. Therefore, if you need any data on this point, you should surely give this map a chance. It also easily serves as a complete summary of any attack you are looking for. It displays the total number of attacks that occurred today till the time, top attacker of the day sorted by country, origin, and destination of the attack, and several other details.
These days, cyberattacks, alongside spam and malware contaminations, are growing quickly, while the digital assault maps will not assist you with alleviating these malevolent dangers, however, the truth of the matter is that it will be definitely helpful to have a view of the top cyber dangers in businesses surrounding us.
While examining these computerized assault maps, it’s getting clear that nobody in this hyper-associated business has ever been protected from cyber threats, subsequently, it is important to think about the guides so clients can without much of a stretch think about the forthcoming dangers or assaults.
Along these lines in the event that you are a piece of any open or private network safety group, at that point start with the fundamentals like analyze your assault surface by actualizing security reviews to defeat the weaknesses in your association.
Consequently, analyze these digital assault guides, and it will without a doubt assist you with recognizing the assaults.
If you like this article, follow us on Twitter, Facebook, Instagram, and LinkedIn.




