OSINT Framework- How to use it?

OSINT Framework, as its name suggests, is a cybersecurity platform, a set of OSINT resources that support the information and data collection activities.
This tool is often used for digital footprinting, OSINT analysis, intelligence gathering, and reconnaissance by security researchers and penetration testers. It offers a simple web-based interface that helps you to access various category-filtered OSINT resources.
It likewise gives an incredible grouping of all current intel sources, making it an extraordinary asset for realizing what aspects of infosec you are neglecting to investigate, or what will be the following proposed OSINT steps for your investigation.
OSINT Framework is ordered dependent on various subjects and objectives. This can be handily observed while investigating the OSINT tree accessible through the web interface.
Get-together data from a tremendous scope of sources is tedious work, yet there are numerous tools to make intelligence gathering less complex. While you may have known about tools like Shodan and port scanners like Nmap and Zenmap, the wide set of software is comprehensive. Luckily, security researchers themselves have started to document the available resources.
An extraordinary spot to begin is the OSINT Framework assembled by Justin Nordine. For a broad range of activities, from gathering email addresses to looking for social media or the dark web, the system offers access to a vast collection of services.
There are a few features you should know; look at the following indicators on the right side for some of the resources listed:
(T) – Indicates a link to a tool that must be installed and run locally
(D) – Google Dork (aka Google Hacking)
(R) – Requires registration
(M) – Indicates a URL that contains the search term, and the URL itself must be edited manually
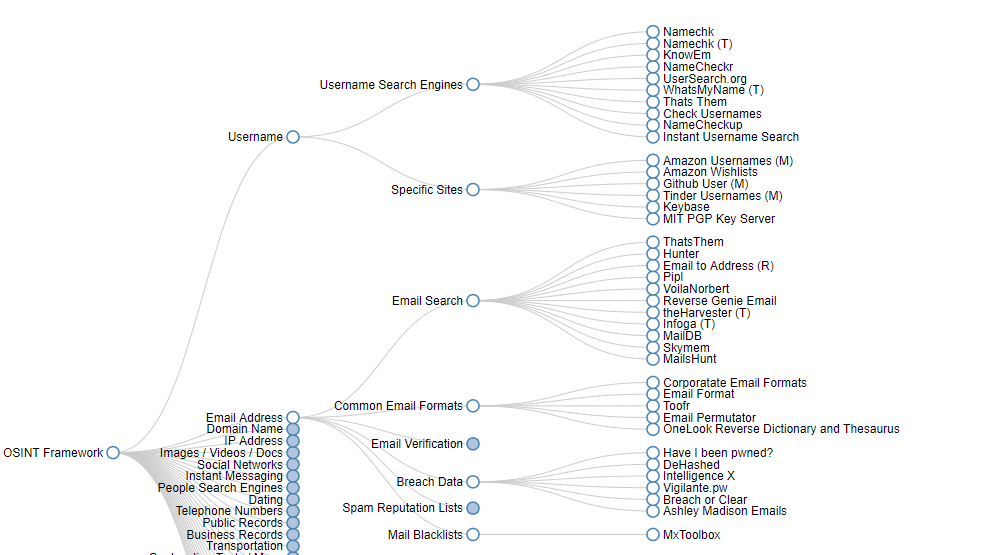
At the point when you click any of the classifications, for example, Username, Email Address, or Domain Name, a lot of helpful tools will appear on the screen, in the form of a sub-tree.
As you have all the resources available in a single interface, it becomes super easy to scan for users, email addresses, IP addresses, or social network records. It is almost like a huge library of OSINT bookmarks.
E.g., you can find links to Cloudflare Watch and Cloud Fail inside the IP Address, explicitly from the Covered by Cloud Services portion.
The equivalent occurs with other well-known classifications. Example, in Email Address – BreachData. In this, you can see several links to helpful services such as Have I been pwned? or DeHashed.
Here are some additional tools that could help you to gather intelligence more effectively such as:
Shodan– Shodan search attempts to capture data such as the service, software, version number, or other information from the ports it examines. The tool comes with filters that help to narrow down the results, such as country, port, operating system, product, version, hostnames, etc. It reveals a huge amount of publicly accessible unprotected knowledge and connections to web interfaces of IoT devices with weak or default keys, devices such as people’s home webcams, and other unsecured appliances.
Maltego– It is an aggregator of interfaces to a few OSINT databases which cover infrastructural reconnaissance. This device can gather an abundance of sensitive data about any objective association, for example,
- Email addresses of employees,
- Confidential files that have carelessly been made publicly accessible,
- DNS records, and
- IP address information.
Metagoofil– It is another OSINT device that uses the Google search engine to remove metadata from openly accessible documents (.pdf, .doc, .xls, .ppt, and so forth) belonging to every target organization. After downloading the documents to the local disk, it pulls out the metadata utilizing different libraries like Hachoir, PdfMiner, and so forth and creates a report.
It should be obvious by perusing the OSINT Framework site- there are practically boundless approaches to get information about any objective you’re researching.
Besides, this structure can be utilized as a decent cybersecurity checklist to perceive what areas you have left to investigate while examining any individual or organization.





One Response
[…] Hack Report, a cybersecurity news publication, has spotlighted an open-source intelligence framework focused on gathering information from free tools and […]