Lazarus abuses authentic security feature in a supply-chain attack

Lazarus, also known as Hidden Cobra, is an umbrella term for select threat groups- including offshoot entities – suspected of being tied to North Korea. Thought to be responsible for Sony’s infamous 2014 hack, Lazarus has also been connected to hacks using zero-day vulnerabilities, LinkedIn phishing messages, and the deployment of Trojans in campaigns including Dacls and Trickbot.
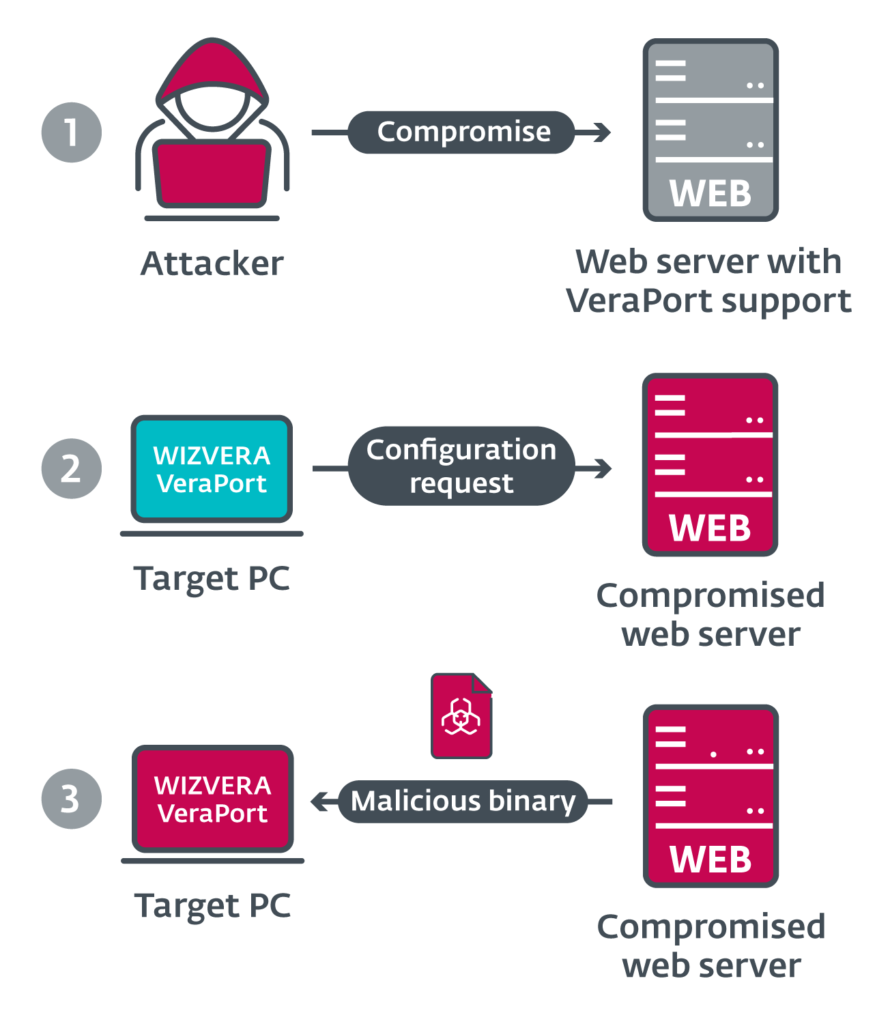
ESET researchers have recently identified attempts to deploy Lazarus malware in South Korea via a supply-chain attack. The attackers used an uncommon supply-chain system to distribute their malware, exploiting legitimate South Korean security tools and digital certificates stolen from two separate companies. As South Korean internet users are frequently asked to install additional security software while visiting government or internet banking websites, the attack was made simpler for the Lazarus group.
You should be aware that WIZVERA VeraPort, referred to as an integration installation program, is a South Korean framework that helps handle such additional security software to understand this novel supply-chain attack. When WIZVERA VeraPort is installed, users obtain and install all necessary software needed by a website. To initiate such software installation, minimal user interaction is needed,” explains Anton Cherepanov, ESET researcher who led the attack investigation.” Usually, South Korea’s government and banking websites use this program. “Some of these websites must have WIZVERA VeraPort installed,” adds Cherepanov.
Additionally, to encrypt the malware samples, the attackers used illegally acquired code-signing certificates. Interestingly, one of these certificates was granted to a South Korean security company’s U.S. branch. “It’s the combination of compromised websites with WIZVERA VeraPort support and specific VeraPort configuration options that allow attackers to perform this attack,” adds Kálnai.
To attribute the attack to Lazarus, ESET Research has clear indicators, as it is a continuation of what KrCERT has called Operation BookCodes, attributed by others in the cybersecurity research community to Lazarus. The other reasons are typical toolset characteristics; detection of the fact that the attack took place in South Korea, where Lazarus is known to operate; the unusual and custom nature of the intrusion and encryption methods used; and the setup of network infrastructure.
Supply chain Attack
The first stage in the attack is for the Lazarus operators to corrupt a site running the Wizvera program. Researchers conclude that this is likely done by tried-and-true spear-phishing attacks that trick website administrators into uploading or linking malicious files to a booby-trapped website that hosts an exploit kit. As attackers enter a foothold on a targeted server, on a compromised website, malicious binaries that appear to be legitimate and use the stolen digital certificates are planted and automatically pushed to unsuspecting site users.
The attackers camouflaged the samples of Lazarus malware as legitimate software, researchers wrote. These samples have similar filenames, icons, and VERSION INFO tools that are often delivered through Wizvera VeraPort as legitimate South Korean applications. Downloaded and executed binaries through the Wizvera VeraPort mechanism are stored in %Temp%\[12 RANDOM DIGITS]\.
When a victim visits an affected site, JavaScript and a WIZVERA configuration file are prompted to download the Wizvera browser plug-in. The update is a base64-encoded XML file that contains the address of the website, a list of installation tools, download URLs, and other parameters, ESET wrote. The researchers mentioned that “These configuration files are digitally signed by Wizvera.” They are tested using a powerful cryptographic algorithm called RSA once downloaded, which is why attackers are unable to easily change the content of these configuration files or set up their own fake website. The attackers, however, may substitute the program from a legitimate but compromised website to be distributed to Wizver VeraPort users.