KashmirBlack Botnet targets CMS vulnerabilities
Imperva security researchers discovered a botnet that exploits vulnerabilities in the underlying content management systems of websites and then uses these compromised servers to mine for cryptocurrencies or deliver more spam to victims.
The botnet, which the researchers dubbed KashmirBlack, began operating in November 2019 and since then infiltrated thousands of websites by targeting vulnerabilities in content management systems including WordPress, Joomla, PrestaShop, Magento, Drupal, vBulletin, OsCommerce, OpenCart, and Yeager.
The researchers estimate that each day, KashmirBlack infects about 700 vulnerable servers, which means that the botnet is responsible for 230,000 infected servers.
“It utilizes dozens of known vulnerabilities on its victims’ servers, performing millions of attacks per day on average on thousands of victims in more than 30 different countries around the world,” according to the Imperva researchers, who note that most of the targeted and compromised servers are within the U.S.
The botnet is controlled by a single command-and-control server, but it is also supported by 60 other compromised servers as part of its malicious infrastructure.
The researcher of Imperva states, “It manages hundreds of bots, each of which interacts with the command-and-control server to obtain new targets, carry out brute force attacks, add backdoors, and extend the botnet scale.”
The KashmirBlack botnet appears to have originated in Indonesia and is run by a hacking group named “PhantomGhost”. The study states that by tracing IP addresses used during a website defacement campaign earlier this year, the researchers were able to link the botnet to this hacking group. Researchers have found that cloud services such as GitHub, Dropbox, and Pastebin are used by the operators behind KashmirBlack to conceal the infrastructure from security tools as well as to send extra commands to infected servers.
How KashmirBlack Works
The Imperva researchers found that the KashmirBlack botnet operators exploit over a dozen common vulnerabilities in websites and then use those compromised servers to help create and sustain the infrastructure of the botnet.
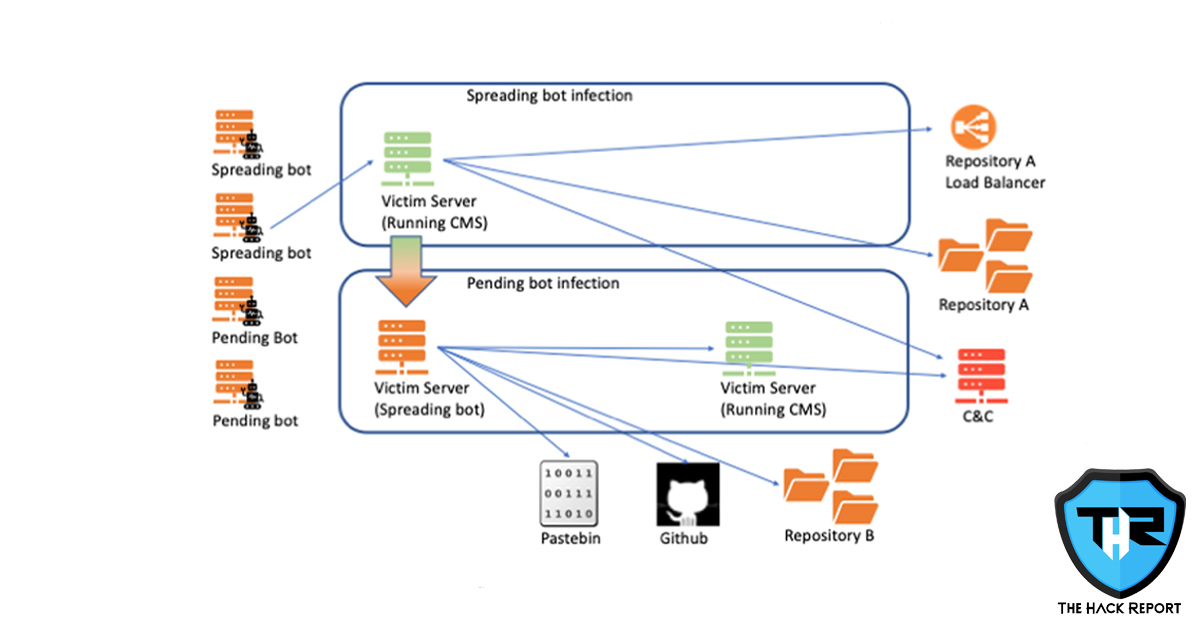
The infrastructure of the botnet is scalable and includes different components. For example, KashmirBlack ‘s infrastructure uses what researchers call “Repository A” to help store malicious scripts to communicate with the command-and-control server, “Repository B” is used to store packages of vulnerabilities and payloads to attack other compromised systems and infect them.
KashmirBlack also uses two bots that help it spread. When a new server is ready to join the larger botnet, a’ spreading bot’ interacts with the command-and-control server and reports back to its operators. A ‘pending bot’ awaits orders to determine if the compromised server should be used as part of the overall infrastructure or allocated to other tasks, such as cryptocurrency mining. To ensure that it runs effectively, the botnet has load-balancing features and it can scale and integrate new exploits for vulnerabilities.
In September, the KashmirBlack botnet experienced a major change when its operators moved the command-and-control server to Dropbox, allowing it to more easily send and fetch commands.
The report found that “moving to Dropbox enables the botnet to hide illegitimate criminal activity behind legal web services.” This is yet another step towards camouflaging botnet traffic, protecting the operation of command-and-control, and, most importantly, making it difficult to track the botnet back to the hacker behind the operation.
According to the study, the KashmirBlack botnet performs multiple functions, including sending out additional spam to its operators as well as defacing websites. Apparently, in March, the botnet added a crypto-mining feature to mine for monero, using XMRig malware. Researchers from Imperva traced this operation to a digital wallet. Security researchers have identified other XMRig botnet operators for their own illegal virtual currency mining activities.




