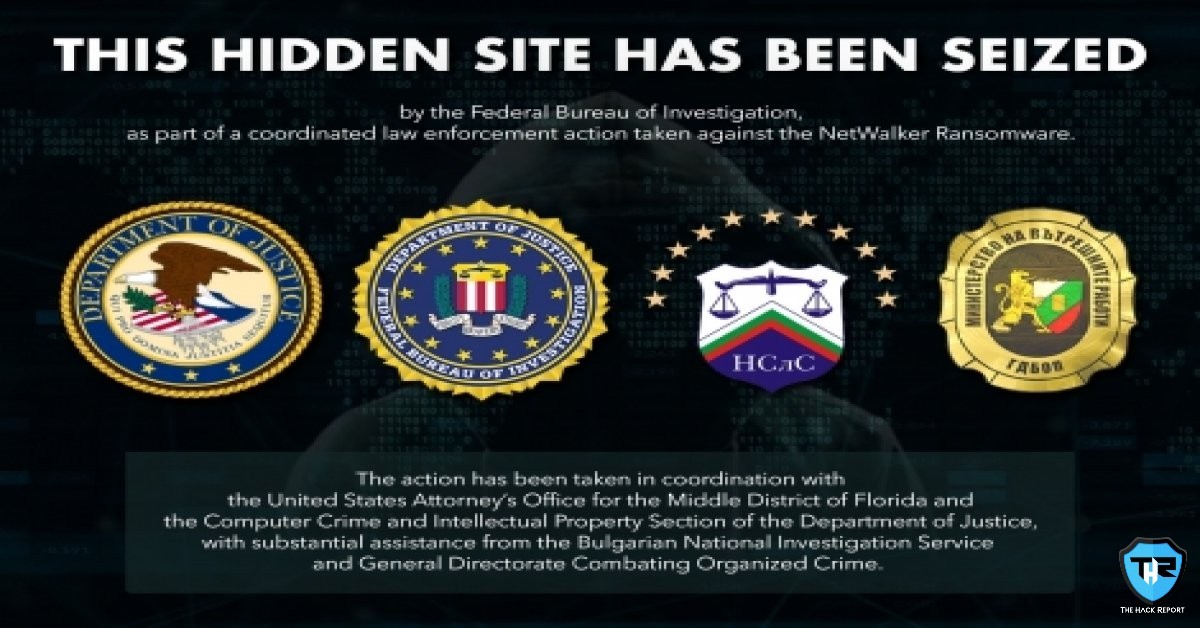
Dark-Web Website Connected With The Netwalker Ransomware, Seized By Authorities
Authorities from the US and Bulgaria recently seized a dark web website which was utilized by the cybercrime group behind the Netwalker ransomware to distribute and sell the stolen/breached data. Nicholas L. McQuaid, the Acting Assistant Attorney General at the Criminal division of the Justice Department explained that “ransomware victims should know that coming forward…
Read more












Recent Comments